Your guide to account takeoverThe rise of account takeover fraud means it’s time to embrace behavioural biometrics
Guide
What is account takeover and how does it happen?
Cybercriminals no longer need to “steal” credit cards to profit. Instead, they take over accounts people already own — banking apps, e-commerce logins, streaming services, even loyalty programs. With stolen credentials bought on the dark web, fraudsters slip into accounts unnoticed, change the settings, and quietly siphon value. By the time the real owner realises, the damage is often done. This is account takeover fraud: stealthy, scalable, and increasingly common.
For businesses, supporting customers dealing with account takeover (ATO) fraud brings rising costs, including chargebacks, reimbursement costs and operational expenses. But it also raises the risk of damaged reputations and eroded customer trust too. As businesses increasingly shift customers to digital platforms, the responsibility lies in offering both security and convenience. That’s why it’s time we all embraced behavioural biometrics, backed with robust device intelligence.
Over the last five years, ATO fraud has overtaken traditional fraud methods to become one of the most serious threats to consumers and businesses across all sectors. In 2024 alone, reported SIM swap fraud increased by over 1000%[1] in the UK, with nearly 3,000 cases logged in the National Fraud Database. That’s not just a temporary blip. It’s a wake-up call for anyone operating in financial services, telecoms or any sector that handles sensitive customer data.
Globally, businesses are already losing billions to ATO each year – and that figure is growing. This can translate into higher costs for services, higher insurance premiums, and even hits to stock values in severe cases. Tackling ATO effectively means fewer losses, happier customers and a stronger brand reputation for security. Clearly, there is a need for a smarter approach to user account security in an increasingly digital-first world.
What is account takeover?
Account takeover (ATO) attacks are a form of fraud where a criminal gains unauthorised access to a legitimate customer’s account and uses it for malicious purposes. These attacks typically involve identity theft, where fraudsters use stolen personal information to access accounts and perform unauthorised transactions.
What’s causing the rise in ATO fraud?
Scammers thrive in times of change. Whenever businesses adopt new technologies, launch digital products or shift customer behaviour, there are new opportunities for fraud. Change creates gaps between systems, teams and in customer understanding. Fraudsters are quick to exploit those gaps before defences catch up.
In recent times, there has been a rush for businesses to adopt digital solutions and transition their customers to them. This has made it easier for people to access the services they need than ever before, but it’s also contributing to a rise in ATO fraud.

More digital touchpoints = more vulnerabilities
As businesses expand their digital offerings through mobile apps, online banking, e-commerce platforms and customer portals, they create a larger digital footprint to protect. Every new login page, payment system, or self-service feature is a potential target for fraudsters looking to exploit vulnerabilities. Credential stuffing also means that one entry point can lead to more breaches across digital services.
Today, many of the security tools we all rely on are struggling to keep up with fraudsters. Traditional bot detection systems can be bypassed using automated tools that solve CAPTCHA or constantly switch IP addresses to avoid detection. These methods mimic legitimate user behaviour, making it harder for standard bot mitigation tools to tell the difference between a real customer and an automated attack.
Consumers really like convenience
Many digital solutions are built for speed and ease of use. While this benefits customers, it can sometimes come at the cost of robust authentication. For example, one-click logins, SMS PINs, or app-based two-factor authentication (2FA) are widely used but increasingly vulnerable to attack.
Customers also often use the same login credentials across multiple platforms and link 2FA for different accounts to the same device, leaving them open to credential stuffing.
We live in digital ecosystems
In a digital-first world, customer identity is everything. Fraudsters know that getting access to a verified account unlocks far more value than a single transaction. ATO allows them to hijack and move invisibly within digital ecosystems. Once inside, they can make fraudulent purchases, transfer money or exploit loyalty points or discounts undetected; then change email addresses and contact numbers so the rightful account owner gets locked out.
Customers expect businesses to handle security
As businesses push more activity online, customers expect those experiences to be secure. But many still place false confidence in SMS PINs or app-based logins. When an ATO incident happens, it’s the business that’s blamed – especially if customers weren’t educated on how to protect themselves or weren’t offered stronger security options.
What does a typical ATO attack look like?
Our latest Fraud and FinCrime Report found that 62% of digital retailers, 48% of banks, and 44% of telecom providers report being targeted by fraudsters in Q1 2025. This means that your customers are under threat of ATO right now. Protecting them isn’t just about fraud loss prevention – it’s vital to maintaining the trust that underpins your customer relationships.
When a customer falls victim to ATO fraud, the impact on them goes far beyond inconvenience. Customers often hold the business responsible for keeping their accounts secure. And once that trust is lost, it’s incredibly hard to win back. Higher customer churn, damaged brand reputation, and potential long-term revenue loss are real possibilities for businesses that fail to take proactive measures on ATO.
The typical ATO attack is not a single event. Instead, it is a chain of actions that need to be ticked off for the attacker to succeed. Understanding what is happening at each stage, as well as what vulnerabilities are being exploited, allows businesses to design better systems.
Here’s what typically happens:
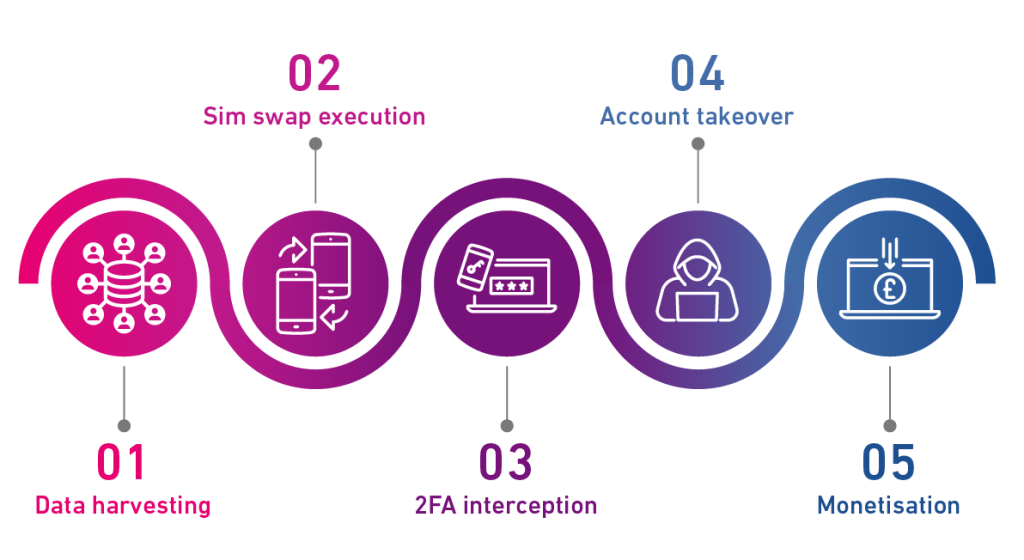
1. Data Harvesting
Fraudsters begin by collecting personal data through phishing emails, spoofed websites, malicious apps or exploiting other data breaches.
2. SIM Swap Execution
Posing as the victim, the scammers convince mobile providers to transfer the number to a new SIM they control.
3. 2FA Interception
With the number hijacked, they can now intercept one-time passcodes sent via SMS – a widely used but increasingly vulnerable authentication method.
4. Account Takeover
With access to credentials and two-factor codes, the scammers can reset passwords, take control of accounts and lock out the legitimate user.
5. Monetisation
The scammer is now free to use the compromised accounts to make purchases, launder money or perform other illegal activities until the attack is discovered.
Traditional authentication isn’t enough anymore
The whole process hinges on authentication that we have all come to accept, but that is no longer fit for purpose. SMS-based 2FA can be easily bypassed. Knowledge-based questions can be guessed using publicly available or stolen data. Device-based authentication can increasingly be impersonated or stolen. The result is a false sense of security for consumers and rising fraud losses for businesses. However, consumers are still placing trust in outdated systems. Despite growing risks, 74% continue to rely on SMS-delivered PIN codes.
Technology also continues to evolve at breakneck speed. Fraudsters are now exploiting generative AI tools, such as deepfake videos to cloned voices, to launch sophisticated social engineering attacks. In one reported case, an employee at a UK engineering firm was tricked into transferring £20 million[2] after a video call with AI-generated avatars of their executive team.
The challenge for businesses is clear. The threat landscape is changing, but our most-used authentication methods are not. Static, one-time defences are no longer sufficient to deal with credential-stuffing attacks, sophisticated phishing campaigns and social engineering that uses emerging technologies to exploit human behaviour. To stay ahead, organisations need a dynamic, continuous approach to authentication –one that is grounded in recognising and verifying genuine user behaviour.
Behavioural biometrics is a smarter way of combating ATO
Behavioural biometrics is an advanced security technology that analyses how people interact with their devices by tracking things like typing speed, swipe patterns, mouse movements or screen pressure. Unlike traditional authentication, which relies on what users know (like passwords) or have (like phones), behavioural biometrics focuses on something far harder to fake: how users behave. Device intelligence adds another layer of security. It focuses on the device itself, such as the operating system and IP address to monitor a change of use.
These technologies work silently in the background, continuously monitoring for anomalies that might signal fraud. If someone logs in with the right credentials but behaves very differently from the genuine user, the system can flag the session and trigger a response. This enables a proactive response to kick in before any fraud takes place rather than a reactive scramble to limit the amount of damage done.
This is especially valuable in the fight against ATO fraud. Even if a fraudster has stolen a user’s login details, they’ll struggle to mimic the real user’s behavioural patterns and hide the new IP address. That makes behavioural biometrics with device intelligence a powerful, frictionless way to detect and stop intruders in real time. When combined with risk analytics, the technologies offer a dynamic, adaptive defence that helps businesses reduce incorrect alerts, minimise disruption and stay one step ahead of evolving threats.
Multi-layered defence is leading the way
We are pioneering the use of behavioural biometrics alongside device intelligence and AI-driven monitoring. We have developed a multi-layered, intelligence-driven platform that passively monitors how users interact with devices to build a unique behavioural profile for each individual.
Even if a fraudster uses the right credentials, our behavioural biometrics and device intelligence capabilities can detect anomalies that suggest an imposter is behind the screen. It does this through several features:
Advanced behavioural analysis
Tracks everything from keystroke dynamics to scroll patterns and mobile gestures, spotting anomalies instantly.
Device intelligence
Detects SIM swaps, virtual machines, VPN usage and emulators. Uses fingerprinting to flag spoofed or compromised devices.
Real-time monitoring
Uses machine learning to track millions of transactions, flag risky behaviours and uncover coordinated fraud rings.
Adaptive multi-modal authentication
Merges behavioural data, device reputation, location, and more to assign real-time risk scores – introducing friction only when needed.
These capabilities help businesses stop ATO fraud before it’s too late; identifying threats early without disrupting genuine customer journeys. The dynamic, context-aware approach strengthens security while preserving the digital experience. In a time where ATO is a matter of when, not if, you need a future-proof solution that doesn’t just detect fraud – it anticipates it.
Continuous authentication means security doesn’t stop at login. CrossCore monitors user behaviour in real time, detecting anomalies like unusual navigation, device behaviour or remote access, and triggers instant intervention without disrupting genuine users.
Organisations can build smarter fraud strategies by setting custom rules and using insights from each event to continuously improve decisions. CrossCore integrates seamlessly across the fraud ecosystem, supporting the full customer journey, from onboarding and login to payments and ongoing activity.
Unlike traditional tools that rely on cookies, our device intelligence uses three types of fingerprinting, only one of which involves cookies. So even if cookie data is missing, detection remains strong. This makes it harder for fraudsters to hide and easier for businesses to stay ahead.
It’s time for a new approach
ATO isn’t a future risk. It’s already damaging the financial wellbeing of consumers and creating losses for businesses. But even though it is evolving fast, there are potential solutions that can be used today. By moving beyond outdated authentication and embracing technologies like behavioural biometrics and digital intelligence, we can protect users in real time without compromising their experience.
If you’re serious about protecting your customers, your brand and your bottom line, it’s time to move beyond passwords and PINs. It’s time to look at solutions that place the user’s unique behaviour at the heart of fraud prevention. At Experian, we’re helping lead that shift to a smarter, safer digital world.